About Us
At I’curity, we believe in long-term partnerships with our clients by engaging on a shared journey to create a future for both parties that is better than either could have developed alone. We mutually find satisfactory solutions for our customer’s current pain points and future growth security needs to enable the business to be agile in ever changing business environment. Our dedication to excellence in every service helps create synergies of knowledge, security, and adaptability for both parties.
Read More
OUR SERVICES
CIAM ODIP Solution
CIAM Open Digital Identity Platform (ODIP) is built with privacy in mind. Customer registration is seamless and identity verification occurs at external trusted parties such as KYC platforms or Government institutions. Customers can login using their social logins, U2F tokens, Mobile Apps with push notifications and so forth to ensure that an organisation can fully engage, acquire, incentivise a customer to ensure loyalty and enable Click-to-buy. With AI, ODIP provides intelligent analysis and tailored CX.
Read MoreCLIENT TESTIMONIALS
What our clients say about us
We have a great partnerships with many of our clients. And we have formed true friendships and trust. Here’s what they’re saying about us...
GET A QUOTERECENT BLOGPOSTS
Latest News from the Blog
How do you secure different application types with SSO and OAuth?
Applications need to be protected against the OWASP Top 10 vulnerabilities. This is a challenge for most enterprises and usually leads to breaches if not implemented in a standardized fashion. In Part 1 of this blog we will first describe the types of Access...
Why are today’s businesses choosing FOSS?
FOSS At times simply referred to as Open Source or Free Software meant to be used for free and to be modify or even share. Features of open code from various community developers and are able to view, create new functionality, and fix the bugs. There is a lot of great...
Identity and Access Management Success Factors
We believe that for the project to be successful, a number of critical factors must be addressed from a business, legal and technology perspective. These are: Strong executive support. Executives form an important support structure to an IAM...
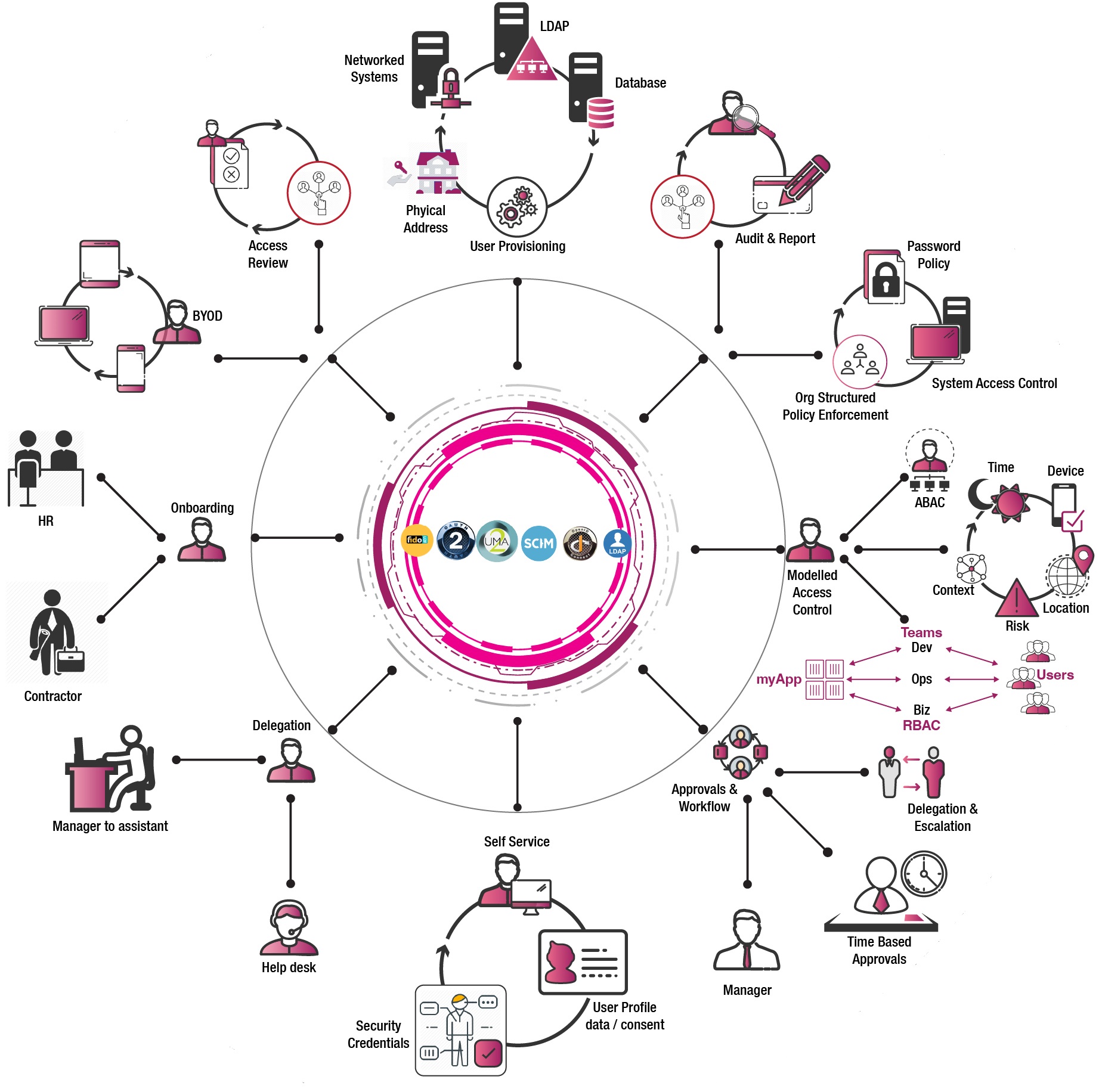
Enterprise Identity and Access Management
When it comes to employee identity and access management operational efficiency, security, BYOD, multiple passwords , massive number of help desk calls, toxic access combination, over entitlements and unmonitored privileged access are some of the pains that most organisations struggle with.
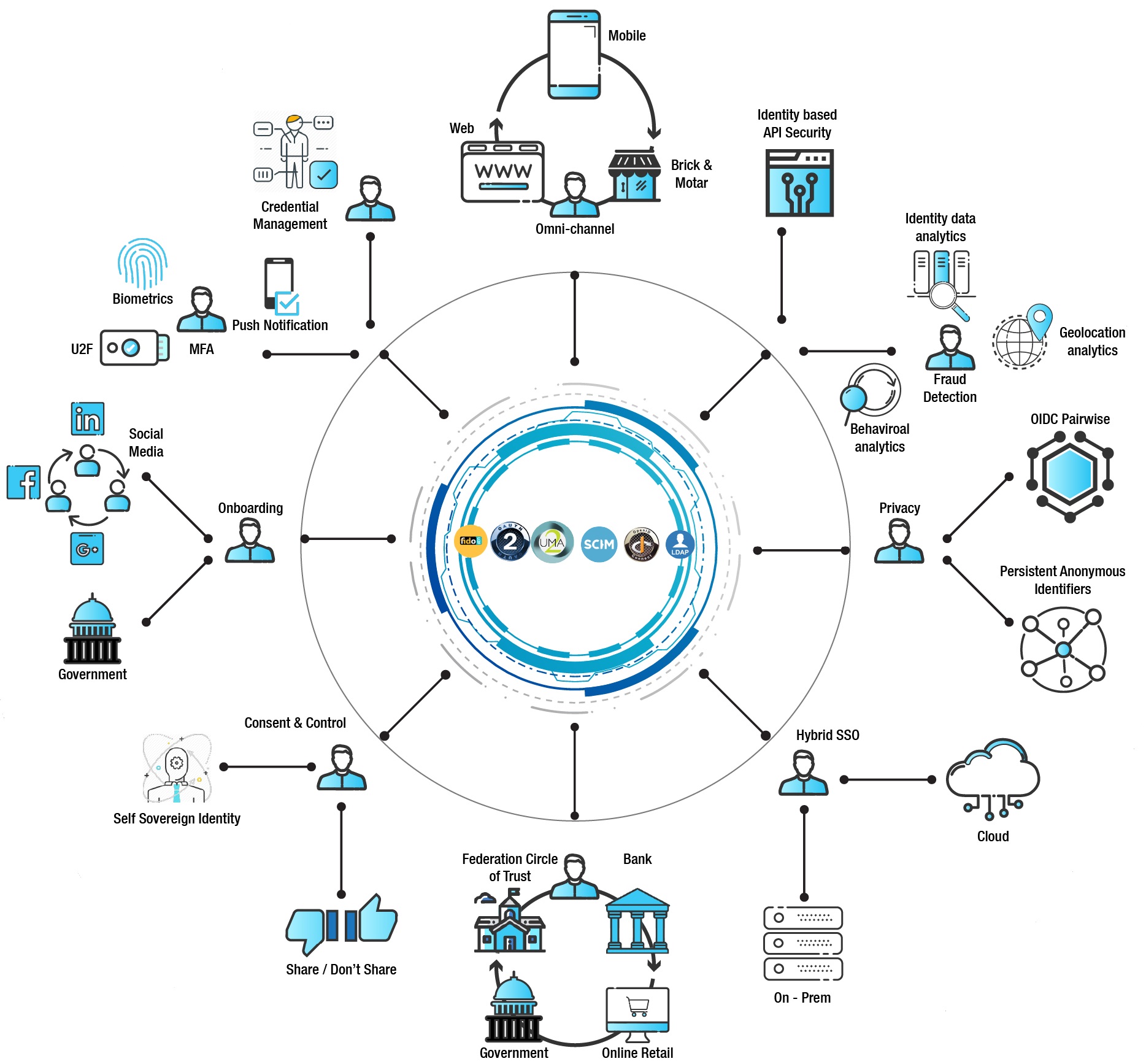
Customer Identity and Access Management
Customers accessing your online services seek frictionless security and great experience. They want to access your services using different channels,
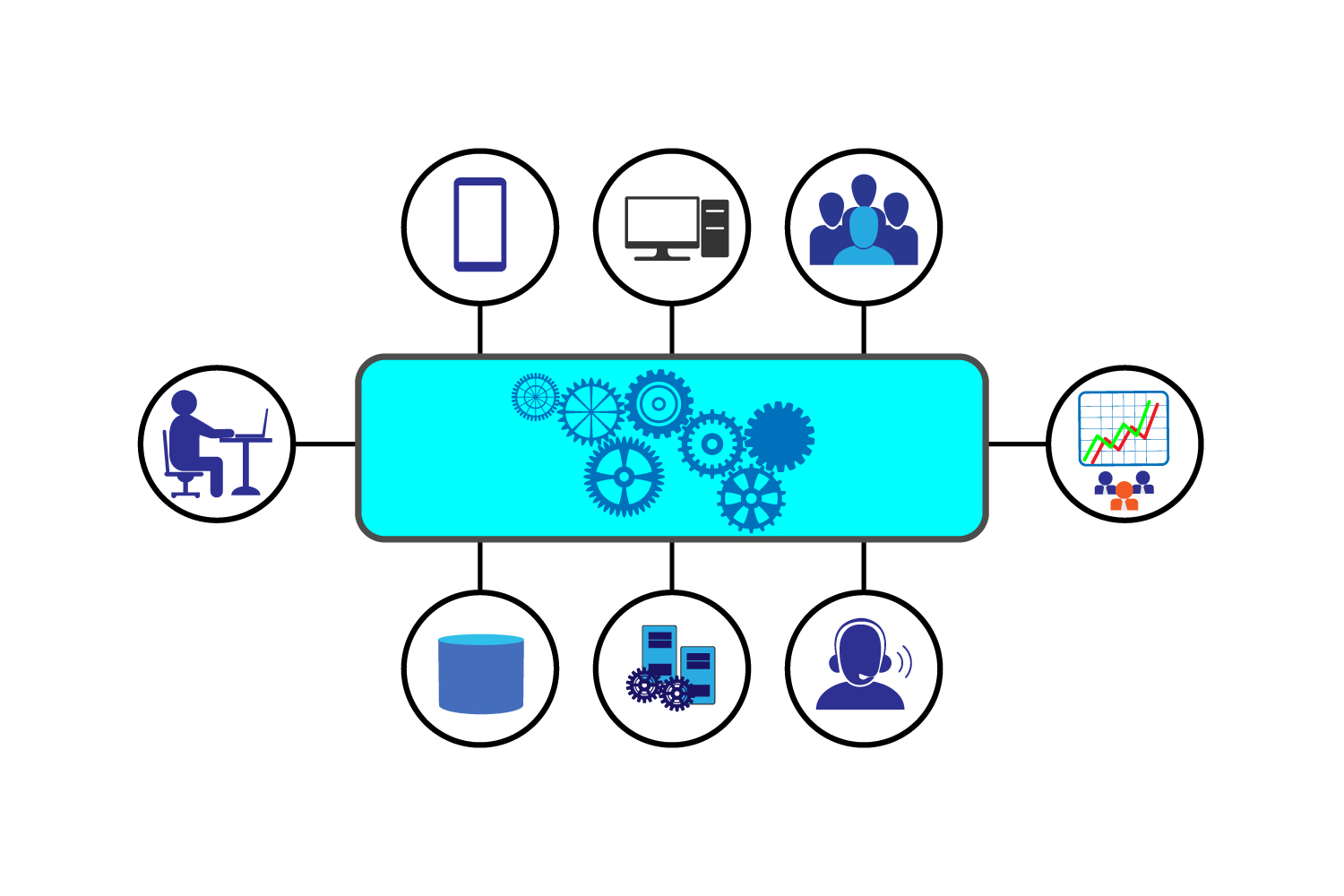
Cloud Native Application Architecture & Security
During your company’s modernisation, you will need to transition your monolithic applications towards a distributed Microservices architecture for portability which is a characteristic of Native Cloud .

Delegations & Impersonations
Delegated access is an important aspect of business operational efficiency. For instance if a line manager goes on leave, they can temporarily delegate their duties to other managers or support staff.
WHAT WE DO
Our Product Features
WE HELP ENTERPRISES STRATEGIZE, PLAN, ARCHITECT AND BUILD IDENTITY AND ACCESS MANAGEMENT AND CLOUD NATIVE PLATFORMS.